In a research survey by Balabit, the most common method of entry into an organization is … Insider Access.
Balabit surveyed whether IT professionals consider the outsider or insider threats more risky – noted that those attacks that are started from outside by attackers primarily targeting insiders’ privileged user accounts (so would never be successful without insider help of insider user accounts misuse), belong to the insider category.
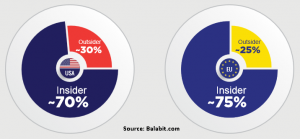
Although, respondents said that they are still afraid of “hackers” breaking into their IT network, the results highlight a good point to an efficient defense strategy: in the USA 70% of those surveyed said that insiders are more risky, and only 30% stated that outsiders pose higher risk. However, this ratio is even more imbalanced in the EU: 75% of respondents consider insiders more risky as opposed to outsider risk with 25%.
It comes as no surprise to those of us in the industry, but whether it’s through weak password, or social engineering, spear-phishing or other means – the weakest point in the information security of your organization is… the insider.
Top methods of exploit for the US are:
- Social Engineering (e.g. Phishing) = 81%
- Compromised Accounts (e.g. weak passwords) = 63%
- Web Based Attacks (e.g. SQL/command injection) = 51%
- Client Side Attacks (e.g. against doc readers, web browsers) = 33%
- Exploit Against Popular Server Updates (e.g. OpenSSL, Heartbleed) = 23%
- Unmanaged Personal Devices (e.g. lack of BYOD policy = 21%
- Physical Intrusion = 15%
- Shawdow IT (e.g. users’ personal cloud-based services for business purposes) = 11%
- Managing Third Party Service Providers (e.g. outsourced infrastructure = 9%
- Take Advantage Of Getting Data Put To The Cloud (e.g. IAAS, PAAS) = 6%
If you’re wondering why this adds up to a lot more than 100%, it’s because multiple factors apply to nearly every attack.
So – have you done any user awareness education lately?