This blog entry is republished here as a training tool – full credit for this article goes to Jame Dupree:
Wikileaks reveals email used to hack Podesta
Tucked away in the twenty-first day of email releases from a top aide to Hillary Clinton today was the email that evidently was used to dupe John Podesta into giving away his password, giving hackers years of behind-the-scenes emails and documents about Hillary Clinton’s quest for the White House.
It turns out, it wasn’t just Podesta’s fault.
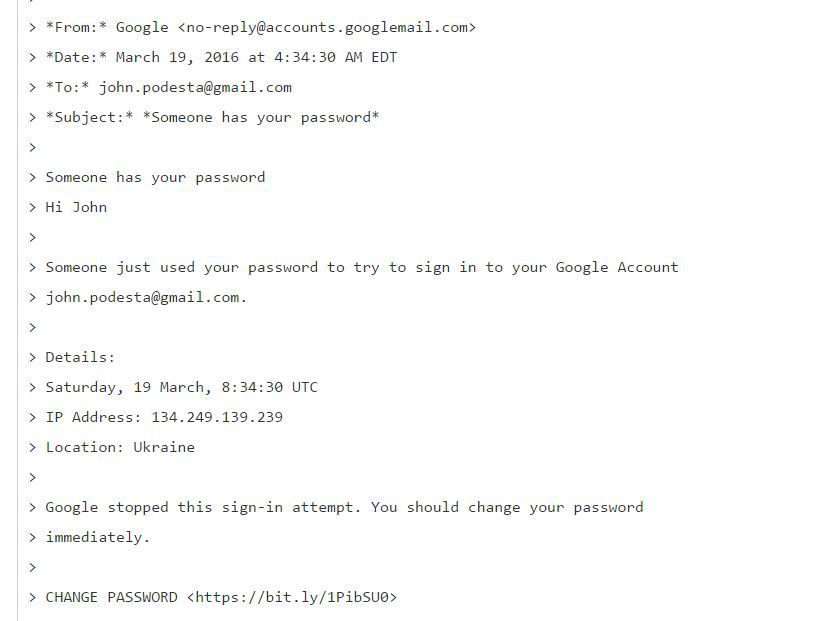
As reported by other news organizations, the hack occurred on March 19, 2016 – with an email that was purportedly from Google, warning Podesta that someone had tried to log into his account from Ukraine.
We finally saw that email today, as part of a later email exchange:
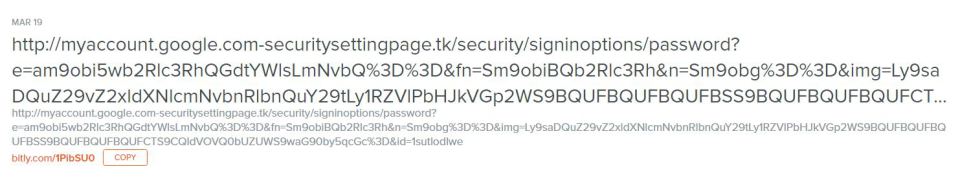
The shortcut “
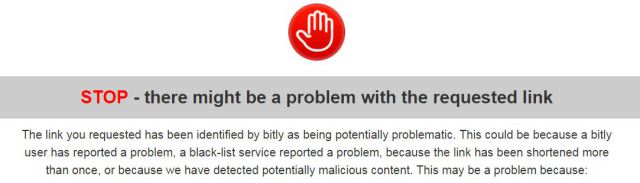
bit.ly/1PibSU0” at the bottom – which supposedly would help Podesta change his password, was really a cleverly designed effort to get him to reveal his password to hackers.That link actually takes you to this link, which, when you click on it, it took me to a warning page:
If you sort through that extensive URL, you see this: “myaccount.google.com-securitysettingpage.tk” – which is a tip off that it is not real.
The domain “.tk” is from Tokelau, an island off of New Zealand – and that’s not where Google is headquartered.
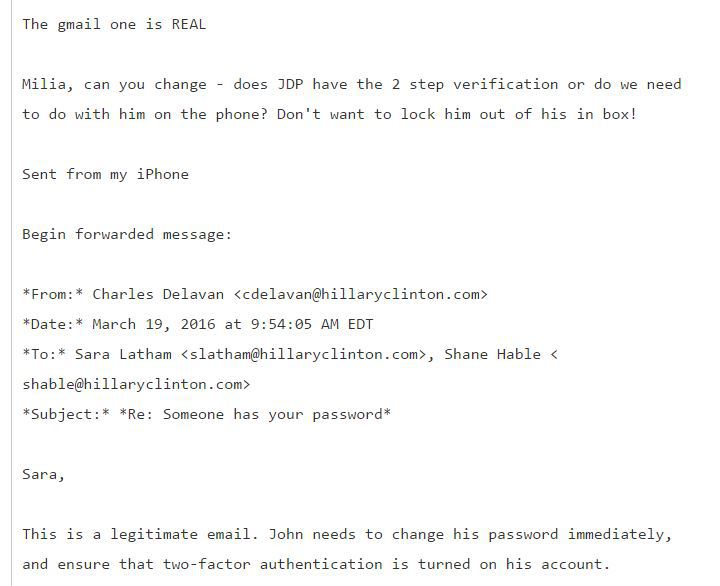
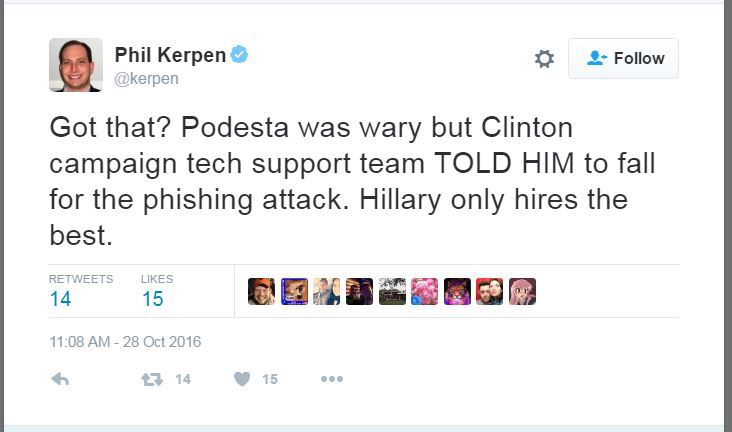
Not only was Podesta fooled, but also it seems the internet experts inside Hillary Clinton’s campaign didn’t recognize it for a Google fake.
“This is a legitimate email,” wrote Charles Delavan, who is identified as a worker on the HFA (Hillary For America) Help Desk.
“John needs to change his password immediately, and ensure that two-factor authentication is turned on his account,” Delavan wrote.
“The gmail one is REAL,” added Sara Latham, another employee with a hillaryclinton.com email address.
Clinton critics jumped on that immediately.
This whole cyberSecurity breach of John Podesta’s emails was given the go ahead by his helpdesk staff member ‘Charles Delevan’. It was a rookie mistake, and even John Podesta himself was suspicious of the email. [this is our sad face]
![]()
So – what is the message from this? Train, train and continue to train. You should never stop cyberSecurity training – even your helpdesk staff are not immune from making mistakes like this… 🙁