We thought now was a good time to re-post a blog post about Java Zero-Day – this blog was originally posted by Stephen Cobb on August 30th 2012 – yes, AUGUST 2012.
Now is the time to disable Java in your web browser, or even remove it from your system if that is practical. Why? The bad guys are hard at work trying to exploit a zero day vulnerability in the latest version of Java (version 1.7, Update 6.). This vulnerability is the subject of a US-CERT Alert (TA12-240A) and ESET researchers have been able to confirm that the Blackhole exploit kit, popular with malware makers, now has the ability to take advantage of the vulnerability.
We hope to publish a detailed technical analysis of the vulnerability (officially known as CVE-2012-4681) here on the blog fairly soon, but in the meantime we wanted to provide some practical advice on how to avoid becoming a victim of the malware that is already being deployed to exploit it. The first line of defense is to turn off Java in your web browser, so we have rounded up instructions on how to do that in the major browsers (Chrome, Firefox, Safari, Opera, and Internet Explorer).
[UPDATE 8/30/2012: Oracle has just announced a Java security update. Although this will fix the CVE-2012-4681 zero day vulnerabilities that prompted this blog post, it does not change our advice that you try living without Java in your browser. If you have Java installed on your Windows system you may want to update to the latest version and then disable it, following the browser disable instructions below. This ensure that any malicious calls to Java which attempt to bypass your browser will encounter the patched version. Mac OS X users who have upgraded to Java 7 should also update to the latest version, but those using Java 6, which was not affected by this latest problem, may want to wait until Apple issues an update.]
Disabling Java in Google Chrome
Google Chrome calls Java a “Plug-in” and to disable Java in Chrome you can access your Plug-in settings by entering “chrome://plugins” in the address field (without the quotation marks) as shown here:

As you can see, Chrome lets you enable or disable each Plug-in that has been installed. Clicking Disable will gray out the Plug-in and prevent it running. As an extra precaution, restart Chrome after disabling the Java Plug-in.
Note that Chrome has an “Always allowed” setting for Plug-ins that are enabled. That’s because Chrome will not, by default, automatically execute potentially risky Plug-ins even if they are enabled. Instead, as a security measure, Chrome will ask permission to execute Plug-ins like Java. You can give permission on a site-by-site basis or activate the “Always allowed” setting. However, I suggest you do not choose the “Always allowed” setting, and go ahead with disabling Java anyway.
Also note that some versions of Chrome exhibit anomalies in the description of the Java Plug-in displayed on this page. Don’t be distracted by these, just go ahead and disable.
Disabling Java in Firefox
The Firefox browser also thinks of Java as a plugin but you disable it through the Add-ons Manager, shown below. You can get to the Firefox Add-ons Manager by clicking on the Firefox button at the top of the browser (use the Tools menu if you are using Firefox on Windows XP), and then click Add-ons. The Add-ons Manager tab will open. In the Add-ons Manager tab, select the Plugins panel:

You may have read that Java can be disabled in Firefox for Windows by using the Windows Control Panel. We don’t recommend that method as it may not be reliable.
Disabling Java in Safari
The instructions for disabling Java in Safari on a Mac can be found on this Apple Support page. If you are using Safari on Windows you can disable Java if you select Edit from the main menu (use the Alt key to display the menu), followed by Preferences. That will get you to the following dialog box (or use the shortcut keystroke combination of Control plus the comma key):
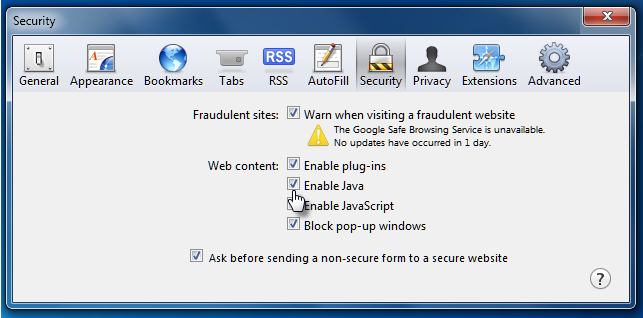
Note that the version of Java in which this latest vulnerability appears (version 1.7) may not be installed on your Mac. Most Macs running Lion or Mountain Lion are running Java 1.6 which is not affected by this particular problem. Apple has not pushed 1.7 to customers and you will only be running Java 1.7 if you went through the installation process yourself. Ironically, this is one of those times when the general advice of experts to “upgrade to the latest version to be secure” does not apply. However, given the eagerness with which the bad guys are digging for vulnerabilities across all versions of Java right now, it makes sense to disable Java in browsers on your Mac regardless of which version you have installed.
Disabling Java in Opera
You can quickly access and change the plug-in settings in the Opera browser by entering “about:plugins” in the address bar (without quotation marks) to display this screen:

Disabling Java in IE
I’d like to say we’ve saved the best for last, but there’s not much to like about disabling Java in IE, something that is clear from the language of the US-CERT in its notes on this latest Java issue. According to Vulnerability Note VU#636312:
“Disabling the Java plug-in for Internet Explorer is significantly more complicated than with other browsers. There are multiple ways for a web page to invoke a Java applet, and multiple ways to configure Java Plug-in support.”
In fact, the task is more than ”complicated” because one of the widely-cited methods for turning off Java in IE–using the Programs section of the Control Panel in Windows 7–is not reliable. We tried turning off Java this way on several different machines and found that the setting was ignored. The detailed instructions provided by US-CERT can be quite daunting for the average user, so seek help with this if you are not familiar with editing the Registry.
Until you can disable Java in IE, avoid using IE as your browser and make sure it is not your default browser (some malware will attempt to execute via the default browser even if you are not using it). The easiest way to make a browser other than IE the default in Windows is to load the browser you want (e.g. Chrome, Safari, or Opera) and make it the default. The steps for doing this vary by browser, but there is a good guide to the default browser settings here.
Removing Java Completely
Of course, one solution to the whole Java-in-my-browser problem is to remove Java from your computer. The only drawback to this solution is that some applications on your system may require Java. For example, your company may have an internal application it developed with Java or you may use one of the “OpenOffice” productivity suites such as LibreOffice. If you can do without Java completely, use the Programs item on the Windows Control Panel to uninstall any item that begins with “Java”:

What’s Next for Java Malware?
We do expect that Oracle will release a fix for this vulnerability in the near future so stay tuned for updates on this topic. (Not that we have heard from Oracle on the timing of a patch, but it makes sense that they will release one sooner rather than later, otherwise there won’t be many Java users left to update.)
We also expect more zero day Java vulnerabilities to appear. And exploitation of those vulnerabilities will happen with considerable speed, as in this case. Why? Because malware is now an industry and as such reaps the rewards of industrial processes, something discussed recently in this article over on SC Magazine’s Cybercrime Corner.

by Stephen Cobb
ESET Security Evangelist
Computer Security Solutions is an ESET Partner – and sells ESET software through a dedicated products portal – BetterAntivirus.com
