Have you been infected by one of the new variants (v3 or v4) of the notorious TeslaCrypt ransomware? If your encrypted files had the extensions .xxx, .ttt, .micro, .mp3 or were left unchanged, then ESET has good news for you: they have a decryptor for TeslaCrypt.
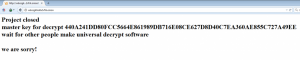
They (and we) have been covering this malware for a few months now, sometimes along with Locky or being spread by Nemucod. Recently, TeslaCrypt’s operators announced that they are wrapping up their malevolent activities:
On this occasion, one of ESET’s analysts contacted the group anonymously, using the official support channel offered to the ransomware victims by the TeslaCrypt’s operators, and requested the universal master decryption key.
Surprisingly, they made it public.
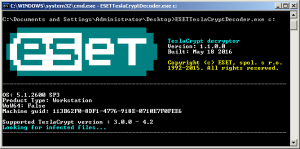
This allowed ESET to create a free decrypting tool promptly, which is able to unlock files affected by all variants of this ransomware. For instructions on how to use the decryptor, please visit the ESET Knowledgebase website.
We must stress that ransomware remains one of the most dangerous computer threats at this moment, and prevention is essential to keep users safe. Therefore, they should keep operating systems and software updated, use reliable security solutions with multiple layers of protection, and regularly back up all important and valuable data at an offline location (such as external storage).
We also advise all users to be very careful when clicking on links or files in their email or browsers. This is particularly true when messages are received from unknown sources or otherwise look suspicious.
For more information about how to protect yourself against these and other ransomware threats, please check this: Things you can do to protect against ransomware.