Blog
Finding the Right Enterprise Security Solutions for Your Organization
If your organization is like most, you’ve got sensitive information populating many areas of your system. You’ve probably got firewalls providing some safety from intruders, but have you developed an enterprise security strategy? Because of the gaps present in many...
Believing Common Cyber Security Myths Can Put Your Organization at Risk
Myths can be a fun pastime to explore, but if you’re following cyber security myths, you could be putting your system and your data at risk. Cyber security myths lend to an already challenging obstacle that many organizations, including small- to medium-size...
How to safely clean your Computer Monitor or TV Screen
When was the last time you cleaned your computer monitor or flat screen TV (or even a curved TV screen)? You’ll be amazed at how much dirt accumulates!
A dirty monitor or TV screen can result in eye-strain and cause head-ache – clean that screen to reduce stress and give your eyes a rest!
Determine Your Digital Resiliency and Strengthen Your Cyber Security Strategy
An area of increasing importance for a more robust cyber security strategy for any organization is in determining your level of digital resilience. This is often carried out via an internal audit that takes into account every aspect of how your organization processes...
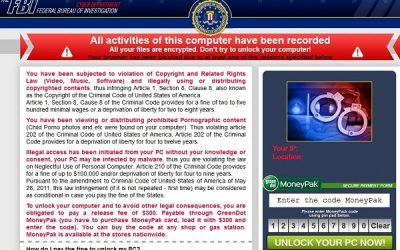
How to Break Out of a Browser Window that’s been Taken Over by a Hijacker
There exist many criminal gangs who attempt to extract money from you, or any unwary internet users. The ways and means which they attempt to do this, are many and varied. The methods these criminals use varies from ransomware to hijacked websites, and everything...
Threat Detection: Utilizing Tools Based on Time
Threat detection is a critical part of any security strategy and business continuity plan, but it requires an awareness of how selected security solutions operate in relation to time. Time is a critical factor, because time to resolution can make the difference...
Finding the Right Cyber Security Solution to Protect Your Organization
Organizations are faced with constant cyber threats, regardless of industry. To better understand how to be proactive in addressing security risks, companies need to understand their data, environment and business needs. Cyber security isn’t a one-size-fits-all...
Improve Cloud Security and Reduce Risk
Cloud computing is being used by organizations across industries, and the advantages are clear. One of the barriers to utilizing cloud-based solutions originally for many organizations was cloud security. Cloud vendors knew that if clients’ data was compromised,...
Follow These Tips to Strengthen Your Cyber Security
Today’s workforce doesn’t only work from the office. Most employees are also working from remote computers, phones and tablets. We’re connected everywhere we go, which means even when we’re “off the clock,” we’re still working. There are obvious productivity...
Computer Security Solutions and Northern Colorado Veteran Resource Center Are Partnering Up
You might think that the New Northern Colorado Veteran Resource Center and a local IT company might be a strange match but that is exactly what happened when NCVRC met Computer Security Solutions, an IT security company from Johnstown.
Protecting Telecom With the Right Cyber Security Tools
Telecom fraud is estimated to cost companies almost $38 billion a year. However, the true cost is immeasurable given the damage caused to the reputation of the hacked organization, which has a trickle-down effect as clients become wary after having their information...
How to Stress the Importance of Cybersecurity to Your Organization
It’s not always an easy sell when it comes to focusing time and money on cybersecurity. Many organizations that are focused on growth initiatives will simply do their best with in-house measures to stay as secure as possible and avoid any spend on cybersecurity....
Tips for a Better Incident Response Strategy
Between cyberattacks, data breaches and factors related to human error, security risks organizations face today are more widespread than ever. Is there enough focus on proper incident response in your industry, and more importantly, across your organization? Many will...
Know the True Costs of Ransomware and How to Prevent It
Wondering what a ransomware attack will cost your company? According to research from Accenture, the costs went up by 27% between 2016 and 2017, and experts expect that trend to continue from 2017 to 2018. Ransomware is widely seen as a lucrative form of cybercrime,...
Antivirus Solutions That Will Work for Your System
Free antivirus software can appear both financially responsible and adequately thorough for your organization’s needs. However, the costs associated with being infected greatly outweigh the money saved. To rely on one of these budget-friendly antivirus solutions is to...
Cyber Security Tips to Keep Your Organization Safe
As the landscape evolves in the area of cyber threats, so too must the approach to cyber security. The danger isn’t subsiding. In fact, it is increasing at a rapid rate and many organizations have felt the impact of how a security breach can affect their business. For...
If Your Cyber Threats Have Doubled, Improve Your Security Strategy
A recent survey by Crowd Research Partners shows that more than half of security operations centers (SOC) polled said detecting cyber threats is the most challenging aspect of their daily tasks. The survey led to a report that found that threat management is a...
Business owners & CEOs often wear many hats, let us take one from you
Any business owner, or entrepreneur will tell you that they many hats ... A highly successful person will know when to delegate a job. When to pass that hat to someone else! IT administration & security is one of those hats that no business owner should wear...
Ready for the right solutions?
It’s time to offload your technology troubles and security stress.
"*" indicates required fields