FBI: No, do not pay ransomware extortionists

The FBI says do not pay ransomware criminals if you get infected.
The ransomware attacks are particularly damaging, of course, because of their payload – encrypting valuable data files and refusing to unlock them unless a ransom demand is met.
Ransomware is explained here:
If your company is unfortunate enough to be hit by a successful ransomware attack, and you didn’t take sufficient precautions to ensure that your backups are not also corrupted (or worse, if you didn’t have any backup at all) then your organisation may be facing a catastrophic situation.
Similarly, if you’re a home user who has their personal computer struck by ransomware, you may find that files which you consider to be priceless emotionally (such a family photos and movies) may be at risk of being lost forever.
It is this, of course, that the criminal gangs behind ransomware attacks are banking on. That you will be so concerned that your company will not be able to do business without access to its data, or that you will be forever sobbing into your cornflakes at the loss of photos of sentimental value, that you will be prepared to swallow the pill and be prepared to pay the extortionists.
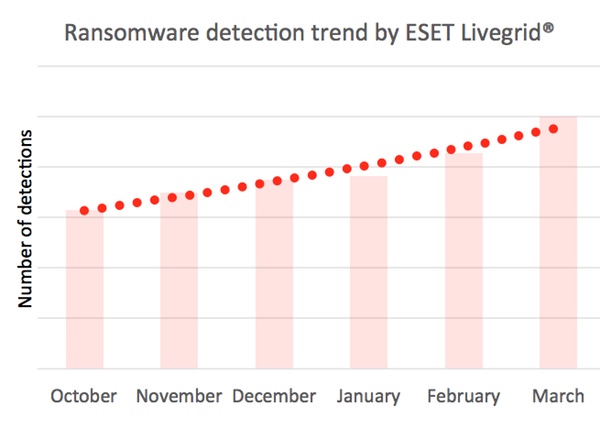
Ransomware is not only on the rise, judging by the number of attacks being reported and the number of new samples being seen in ESET’s labs, but is also becoming more sophisticated and aggressive.
Modern ransomware is not just being spread via malicious emails, but also taking advantage of exploit kits and malvertising campaigns to infect unwary computer users as they visit legitimate websites.
Fortunately, although many ransomware attacks are becomingly more sophisticated, there are also signs that the perpetrators are sometimes not immune from making mistakes themselves.
But if ransomware does manage to encrypt your files, and you cannot access working backups your data, what should you do?
A recent advisory issued by the FBI strongly urges victims of ransomware not to pay the criminals.
The advisory quotes FBI Cyber Division Assistant Director James Trainor, who confirms that the bureau does not recommend paying extortionists:
“Paying a ransom doesn’t guarantee an organization that it will get its data back—we’ve seen cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity. And finally, by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.”
It’s good to hear such a clear statement from the FBI, as in late 2015 the law enforcement agency was widely quoted seemingly saying that it often advised victims to “just pay the ransom.”
Now the FBI has published a list of tips to reduce the chance of ransomware being the ruin of your company (and some of them are applicable to home users too):
- Make sure employees are aware of ransomware and of their critical roles in protecting the organization’s data.
- Patch operating system, software, and firmware on digital devices (which may be made easier through a centralized patch management system).
- Ensure anti-virus and anti-malware solutions are set to automatically update and conduct regular scans.
- Manage the use of privileged accounts — no users should be assigned administrative access unless absolutely needed, and only use administrator accounts when necessary.
- Configure access controls, including file, directory, and network share permissions appropriately. If users only need read specific information, they don’t need write-access to those files or directories.
- Disable macro scripts from Microsoft Office files transmitted over email.
- Implement software restriction policies or other controls to prevent programs from executing from common ransomware locations (e.g., temporary folders supporting popular Internet browsers, compression/decompression programs).
- Back up data regularly and verify the integrity of those backups regularly.
- Secure your backups. Make sure they aren’t connected to the computers and networks they are backing up.
Prevention is always better than cure. Protect your computers – whether it be at home or in the office – from the threat of ransomware, and take the necessary measures so that if you are unlucky to be hit by a ransomware attack, you can recover.
Original Article: We Live Security
Author: Graham Cluley
Republished with Permission of ESET LLC.

