A little over three months ago, I wrote here about how Microsoft’s Digital Crimes Unit, along with its financial industry partners and Kyrus Tech, took action to disrupt the dangerous Zeus botnets, known for fueling half a billion dollars in online fraud and identity left. We are pleased to announce that we have identified and named two defendants as members behind the Zeus botnet family, and that we will also be referring the case to the FBI for criminal review, turning over all of the evidence gathered so far, including evidence of a broader group of perpetrators beyond the named defendants.
A little over three months ago, I wrote here about how Microsoft’s Digital Crimes Unit, along with its financial industry partners and Kyrus Tech, took action to disrupt the dangerous Zeus botnets, known for fueling half a billion dollars in online fraud and identity left. We are pleased to announce that we have identified and named two defendants as members behind the Zeus botnet family, and that we will also be referring the case to the FBI for criminal review, turning over all of the evidence gathered so far, including evidence of a broader group of perpetrators beyond the named defendants.
In an amended complaint, filed last week, Microsoft named Yevhen Kulibaba and Yuriy Konovalenko as defendants. Microsoft has learned that these particular defendants were already serving jail time in the United Kingdom for other Zeus malware related charges. Microsoft has advised the U.K. government of the criminal referral to the FBI. By referring this case to the FBI, as we did in September 2011 with our case against the operators of the Rustock botnet, we are affirming our commitment to coordinating our efforts with law enforcement. Our goal is always to work in ways that are complementary to law enforcement. Our hope is that the evidence we provided to the FBI in this case will lead to a criminal investigation that brings the perpetrators to justice.
The original complaint was filed against a group of “John Doe” defendants, and with the exception of Yevhen Kulibaba and Yuriy Konovalenko, our best efforts to identify the remaining John Doe defendants turned up no response. We will continue our efforts to serve defendants Kulibaba and Konovalenko, and the John Doe defendants, with this amended complaint. Meanwhile, the botnets’ command and control domains remain disabled. It is Microsoft’s goal to ensure that these domains ultimately remain disabled, and we hope the evidence collected from these domains leads to a criminal investigation.
As I’ve written previously, the goal of this operation was not to entirely take out all of the botnets running on Zeus-based malware. Microsoft and our financial industry partners sought to help protect innocent people by disrupting the Zeus business model and increasing the cost of doing business for cybercriminals. I’m happy to report that we are already seeing proof that our disruptive actions were successful in achieving this goal. We mitigated the threat and caused long-term damage to the cybercriminal organization that relies on these botnets for illicit gain.
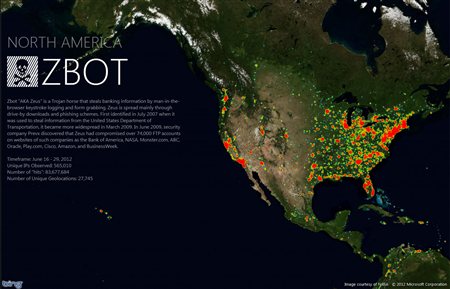
Our co-plaintiff, NACHA – The Electronic Payments Association, reports a 90 percent reduction in innocent victims receiving fraudulent phishing e-mails claiming to be from NACHA. Prior to our disruptive action, monthly averages for scam e-mails were in the hundred million range and peaked at as high as 167 million e-mails in a single 24-hour period in August 2011. Meanwhile, as noted in the chart below, we also see a decline in regards to Zeus infection rates. These successful results represent a significant advancement for the people that Microsoft, the financial industry and law enforcement are all focused on protecting as customers and citizens.
Worldwide Zeus Infections (by observed known IP address infections):
Observed : Mar 25-31, 2012 : 779,816
Observed : June 17-23, 2012 : 336,393
Additionally, as a result of sink holing the Zeus IPs seized during Operation b71, we have learned the locations of hundreds of thousands of computers infected with Zeus malware. These computers belong to innocent people, and we want to rid their machines of the Zeus malware for good. To this end, we will coordinate with Internet service providers (ISPs) and Community Emergency Response Teams (CERTs) around the world to help people regain control of their Zeus infected computers.
It’s important to emphasize that botnets are especially dangerous because people are often unaware that their computer is infected with malicious software, putting their personal and financial information at risk. We encourage you to visit http://support.microsoft.com/botnets for free information and tools to analyze and clean your computer.
As Microsoft and our partners explained in March, Operation b71 is just one step in an ongoing campaign to undermine the Zeus cybercriminal organization and help identify those responsible for this dangerous threat. We are committed in continuing our efforts to work with law enforcement and industry partners to disrupt and disable botnets like Zeus, and to help protect our customers and make the Internet a safer place for everyone.
To stay up to date on the latest developments on the fight against cybercrime, follow the Microsoft Digital Crimes Unit on Facebook and Twitter.
Posted by Richard Domingues Boscovich
Senior Attorney, Microsoft Digital Crimes Unit