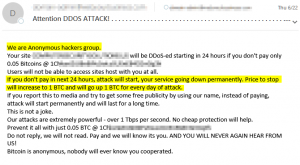
A new email scam is going round, and it hit our desks this week, so we spoke to the FBI about it and then we get a notice from them about this very scam.
The email says it’s from ‘Anonymous’ or ‘Lizard Squad’, a hacker group that they hope you’ve heard of. The email mentioned a domain you own, and says that they will begin applying a denial of service attack unless you send them a bitcoin (btc) payment. In our case, it was 0.05 btc. They promise that if you do not send the money, that the DDoS will continue and their price will increase by 1 bitcoin per day after that. There is a bitcoin wallet listed to deposit the funds into, and the email even says that we need not worry, because bitcoin payments are anonymous.
We should be clear – there is no evidence that these emails actually come from Anonymous, or Lizard Squad, or that they have the capabilities to carry out their DDOS threat. But we recommend if you get one of these, that you contact your local FBI field office. Tell them that you have received an email with a DDOS for Bitcoin extortion and would like to talk to an agent attached to your local Cyber Task Force, or FBI Cywatch.
FBI Recommendations:
The FBI suggests precautionary measures to mitigate DDoS threats to include, but not limited to:
- Have a DDoS mitigation strategy ready ahead of time.
- Implement an incident response plan that includes DDoS mitigation and practice this plan before an actual incident occurs. This plan may involve external organizations such as your Internet Service Provider, technology companies that offer DDoS mitigation services, and law enforcement.
- Ensure your plan includes the appropriate contacts within these external organizations. Test activating your incident response team and third party contacts.
- Implement a data back-up and recovery plan to maintain copies of sensitive or proprietary data in a separate and secure location. Backup copies of sensitive data should not be readily accessible from local networks.
- Ensure upstream firewalls are in place to block incoming User Data Protocol (UDP) packets.
- Ensure software or firmware updates are applied as soon as the device manufacturer releases them. If you have received one of these demands:
- Do not make the demand payment.
- Retain the original emails with headers.
- If applicable, maintain a timeline of the attack, recording all times and content of the attack.