The Shadow Brokers — the mysterious person or group that over the past eight months has leaked a gigabyte of the NSA’s weaponized software exploits—just published a very significant release. Friday’s dump contains powerful exploits and hacking tools that target most versions of Microsoft Windows and evidence of sophisticated hacks on the SWIFT banking system as used by many banks around the world.
Most CyberSecurity experts who examined the dump, said that it contained what appears to be genuine samples of the code — even though they are somewhat outdated — tools of the type that would be used in the production of the NSA’s custom-built malware.
One of the Windows zero-days flagged by Matthew Hickey, a security expert and co-founder of Hacker House, is dubbed Eternalblue. It exploits a remote code-execution bug in the latest version of Windows 2008 R2 using the server message block and NetBT protocols.
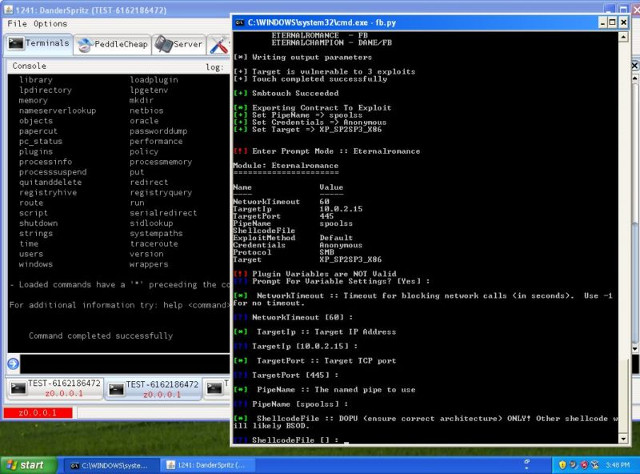
Another tool known as Eternalromance contains an easy-to-use interface and “slick” code. Hickey said it exploits Windows systems over TCP ports 445 and 139. The exact cause of the bug is still being identified. Friday’s release contains several tools with the word “eternal” in their name that exploit previously unknown flaws in Windows desktops and servers.
Having examined the list of tools available to us – there were a number of firewall or UTM device exploits – Fortigate and Cisco seeing a lot of attention from the NSA tools – So far, we have not seen any exploits against the Sophos range of UTMs – which is good! 😀